On September 22, 2023, Linear Finance—a cross-chain asset protocol—reported a malicious attack from the previous day. The attacker managed to mint an unlimited amount of lAAVE and then exchange them for lUSD on the Linear Exchange. This attack resulted in an absolute depletion of lUSD liquidity on PancakeSwap and Ascendex, causing lUSD’s value to plummet to zero.
https://medium.com/linear-finance/%E2%84%93usd-exploit-283f2d32a2f3
The key to this attack lies in the ability of the attacker to mint an unlimited amount of lAAVE tokens. Our main focus here is to delve into the mechanism of the unlimited lAAVE token minting.
Unlimited Minting of lAAVE Tokens: A Closer Look
Main Addresses Involved in The Attack
Attacker address:
0xBd6111dB894D6cc4Aede0D4429F9D7EA55abD41b
Attack contract:
0x58a278A80D2150481cEB9877aCE7d95eed6d5578
Deployer of attack contract:
0xAC70Eba7890B1A4c0416E4e4d1FedD47B1417Fc2
Linear Finance’s access control contract:
0x50bde2dc074c849efc19c554e55f9f1befc7f0bf
The original admin of access control contract:
0x5C9d6aFE82C8f1c33aB274C577932F2D40778347
The new admin of access control contract:
0xc1A4aCafED94E69359361429593433ca5E917DA3
lAAVE token contract:
0x3566c27ccdc102d91728c06f38c9bc907044d796
Attack transaction:
https://bscscan.com/tx/0xb9eac27439da28edad2560c81b6ddb331b33861a78a508ea6e7479d963fe280e
Timeline of The Attack
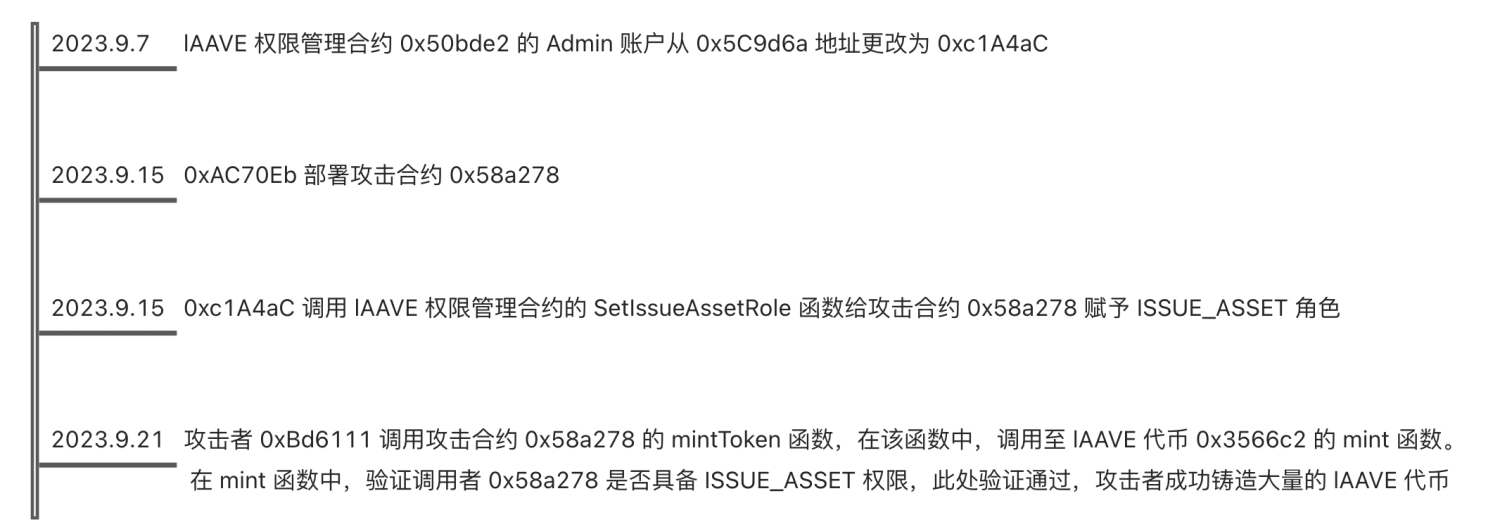
On September 7th, the original admin 0x5C9d6a of Linear Finance’s access control contract invoked the
SetAdminfunction of the access control contract 0x50bde2, transferring the admin role to the new admin address 0xc1A4aC (detailed transaction). The admin of the access control contract has the authority to call theSetIssueAssetRolefunction of the contract, granting the specified address theISSUE_ASSETrole, thereby enabling them to mint tokens.
On September 15th, the creator of the attack contract, 0xAC70Eb, deployed the attack contract 0x58a278 (detailed transaction).
On the same day, September 15th, the new admin of the Linear Finance’s access control contract, 0xc1A4aC, invoked the
SetIssueAssetRolefunction of the access control contract, granting the attack contract 0x58a278 theISSUE_ASSETrole, allowing it to mint tokens (detailed transaction).On September 21st, the attacker 0xBd6111 called the mintToken function of the attack contract 0x58a278, resulting in a significant amount of lAAVE token mint.
By disassembling and examining the code of the attack contracthttps://library.dedaub.com/decompile?md5=63283effc0a281ce6e55249ca3bfc941
We can see that the attacker invoked the
mintfunction of the lAAVE token contract within the attack contract. The lAAVE token contract verified if the caller has theISSUE_ASSETrole. Since the attack contract has already been granted theISSUE_ASSETrole in the 3rd step, the attacker passed the verification and minted a large amount of lAAVE tokens (detailed transaction).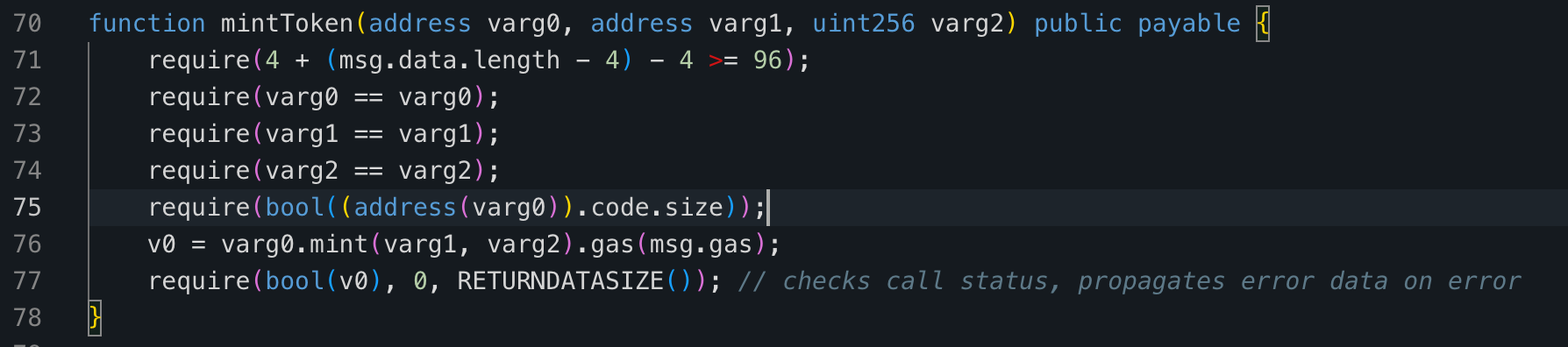
mintToken function of the attack contract 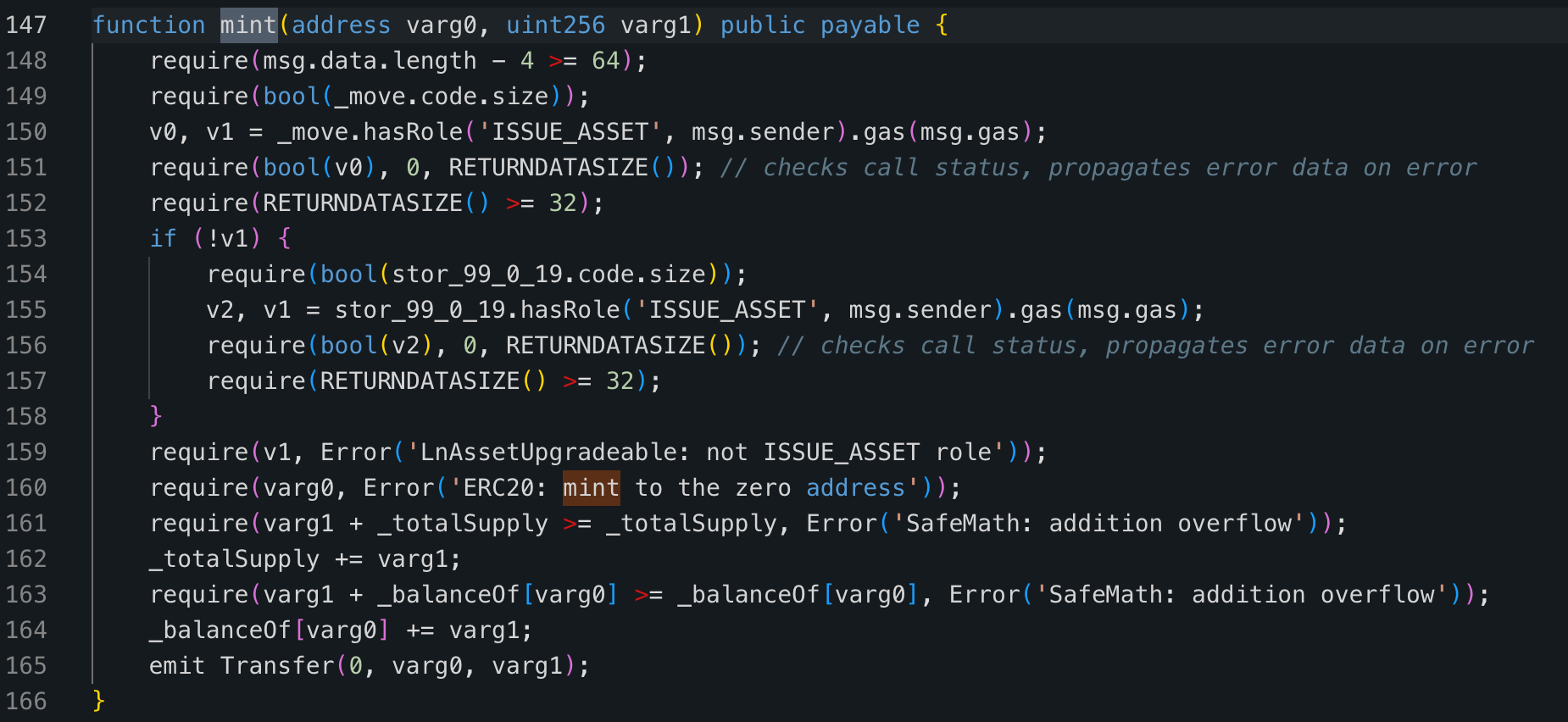
mint function of lAAVE
Conclusion
Tracing the entire attack pathway indicates a strategic transfer of permissions. The primary suspect is address 0x5C9d6a, which handed over admin permissions of the Linear Finance’s permission verification contract to address 0xc1A4aC. This set off a sequence of events: the deployment of the malicious contract by 0xAC70Eb and its subsequent exploitation by 0xBd6111, culminating in the massive lAAVE token mint.
Further investigation of the fund flow across the attack chain revealed that the involved addresses (0xc1A4aC, 0xAC70Eb, and 0xBd6111) all traced back to the Tornado.Cash. Specific transactions highlight this connection (transaction 1, transaction 2 , and transaction 3). Consequently, there’s a strong indication that the trio of addresses implicated in this attack could be under the control of a singular attacker.
Given these findings, we’re led to believe that the private key associated with address 0x5C9d6a (initial admin for Linear Finance’s permission verification) might have been compromised and possibly acquired by the entity behind 0xc1A4aC. This breach appears to be the root cause of the attack.
Recommendations
- Embrace Multisig Wallets: For pivotal permission-based operations in a project, lean on Multisig Wallets over single admin address. It offers an added security layer, ensuring crucial operations get multiple approvals, eliminating single points of failure.
- Robust Permission Checks: Especially for high-risk operations like token minting and burning, implement rigorous permission checks. Alongside, continually test and validate to prevent unauthorized intrusions.